Hey Folks! Today I am going to show how I reverse an android application and got its VIP subscription for free. As It is a real-world application, so I can not disclose the name of the application. Also, I will be not responsible for the usage of the information/data shown here. This is just for educational purpose. Let’s begin the hacking.
Before going in-depth, one thing I must say from my experience is that you don’t need to know everything in reversing, focus on the things/reason(getting VIP/Premium access, customization, searching for keys, etc.) for which you are doing reversing and understand only parts that are necessary for getting those things. Now, let’s go to our android reversing. First, I downloaded the apk from APKMirror, and open It in the JADX tool, JADX is basically dex to java decompiler that helps in producing java source code from apk files. Now, let’s search for some strings like “VIP”, “premium”, etc. On searching for string “VIP” I got the results like this.
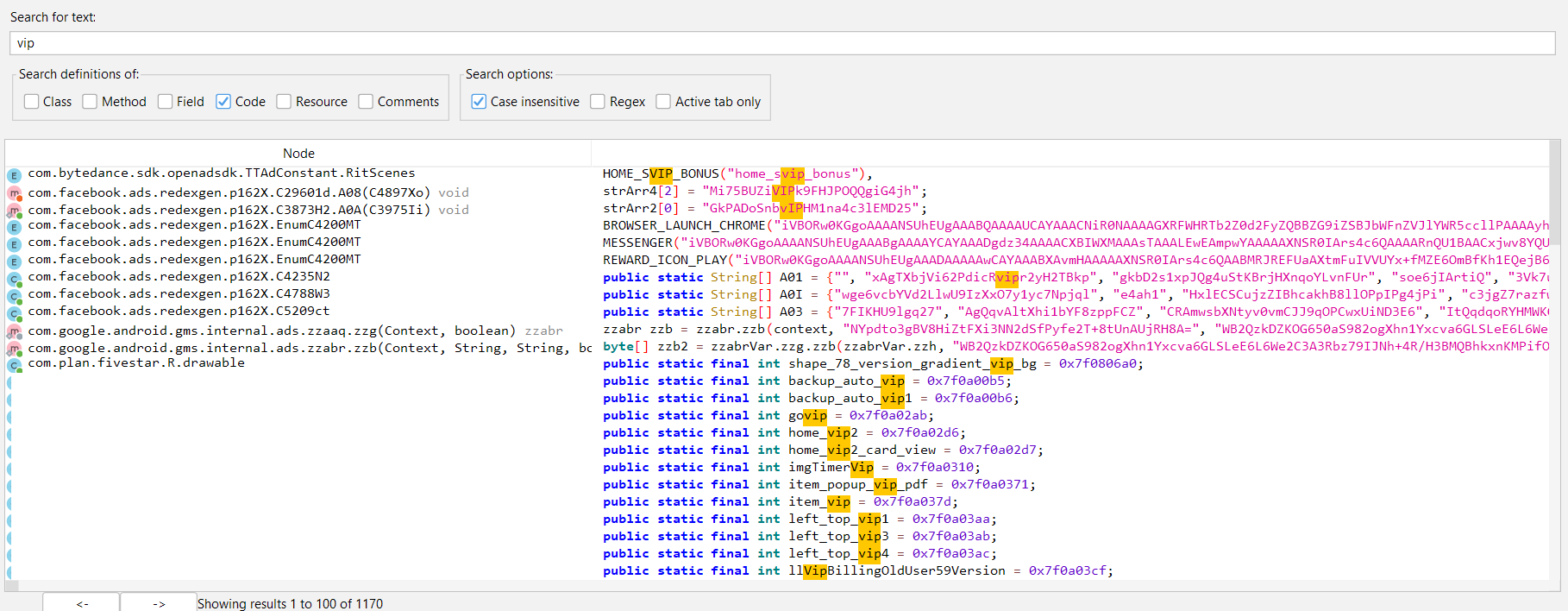
I didn’t get much idea about which functions are checking for VIP access, because of the code obfuscation, but I got the idea, that there is something related to the keyword “VIP”. So, let’s continue the research with that string only.
Now, I also checked the java source code by changing the target.apk file to the target.zip file and extracted the files. On extraction, I got the dex code and I changed them into java class file and opened it with jadx in the hope that it will contain some more information. But there was nothing. Now, I am only left with the idea of extracting the smali code, so let’s do that.
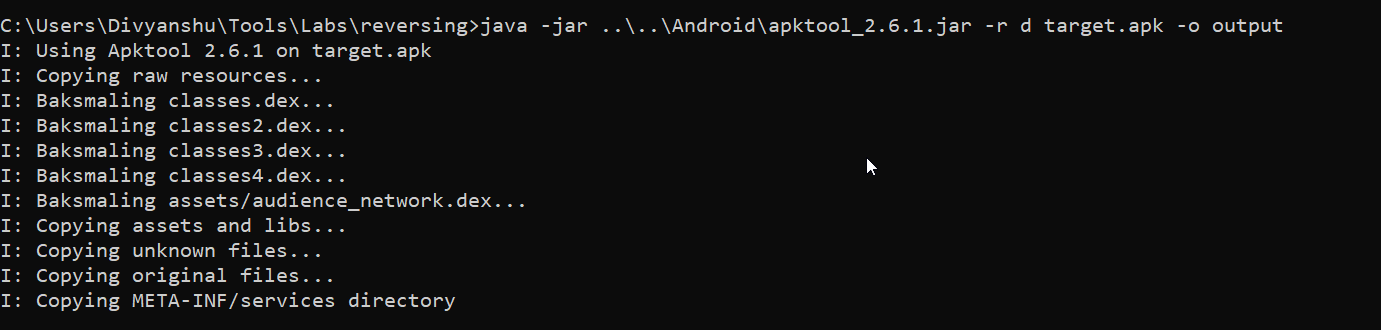
I used the apktool and decompiled the apk and got the smali files (as shown in the below picture). Always, try to use “-r” flag with apktool while decompiling and compiling the apk files, in this way you can avoid the errors related to the resource file of apk.
I opened the output folder in vscode , and start searching for the keyword “API”. In one place I saw, this piece of code is just calling a function “isVip()” and the return type of this function is “boolean” (because of “Z” in the last of function).
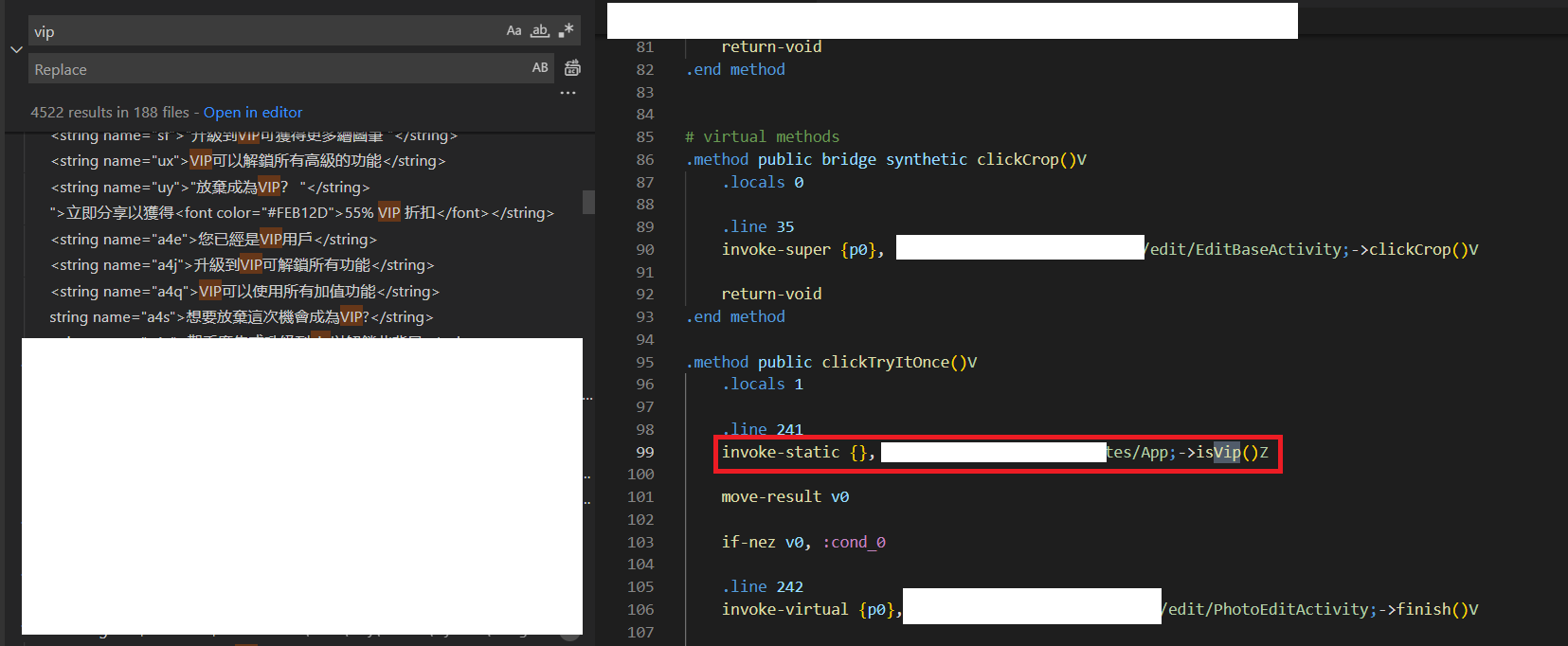
Now, I am sure that some of where “isvip()” function is being used and that function is deciding the VIP status of the application. I started searching for the “isvip()” function in smali files and found the function in APP.smali file.
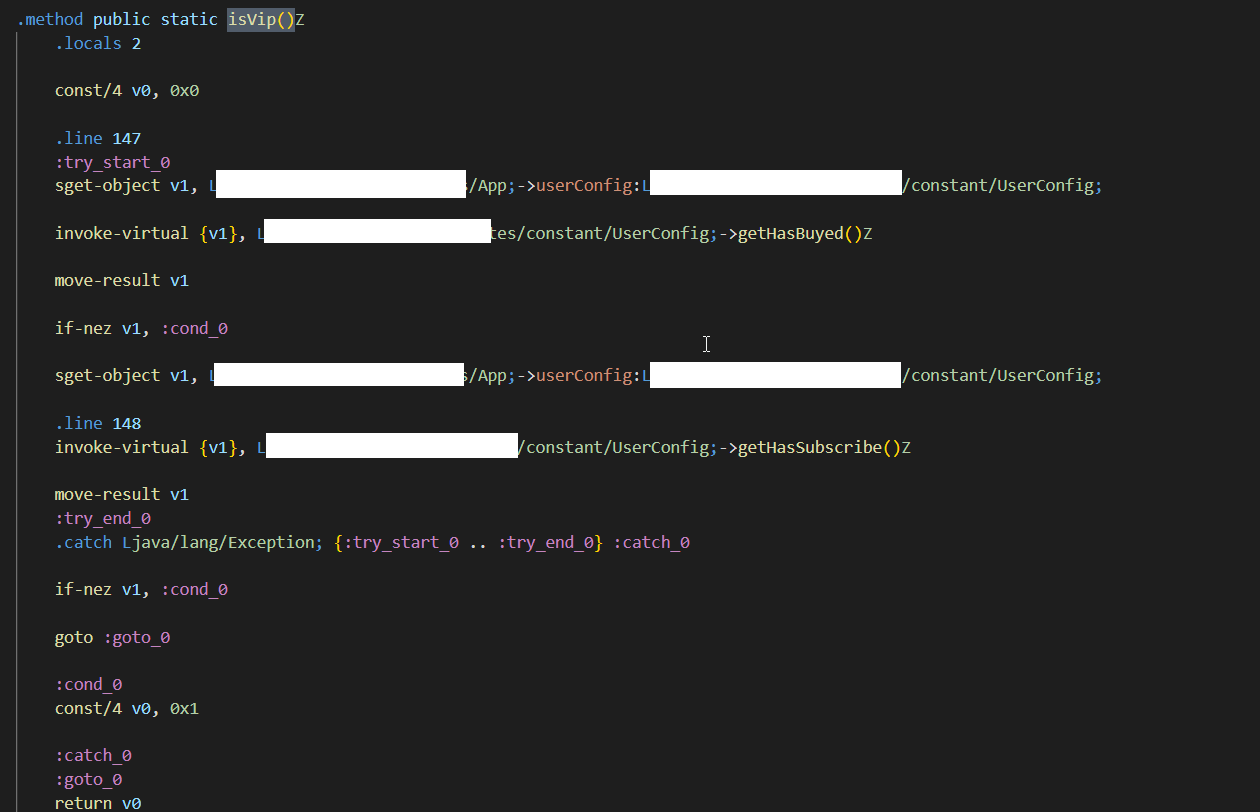
From here, I have two ways of getting VIP access. First, I go and understand each and every piece line of code in this function and make changes to them or I just simply remove all the lines of code in this function and make the function return True in every condition. Yes! You guessed it right, I did it through the second method. I changed the code and make it return True ( as shown in the below picture).
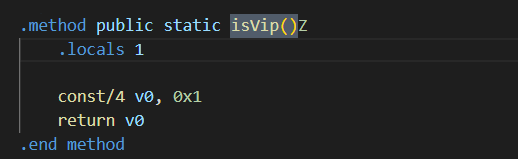
IsVip() is a function name, and “Z” denotes the return type, which is boolean. Local denotes the number of registers used in this function which is (v0), and its value is 0x1 which denotes True or 1.
Note: If you don’t know how to write in smali , you can just simply write the java code and convert the compiled java class file to dex file by using android’s “dx” utility tool and then run baksmali tool on dex files to get the smali files. I did in the same way. Below commands worked for me.
javac --target 7 --source 1.7 target.java
java -jar ..\..\AppData\Local\Android\Sdk\build-tools\30.0.3\lib\dx.jar --dex --output=classses.dex target.class
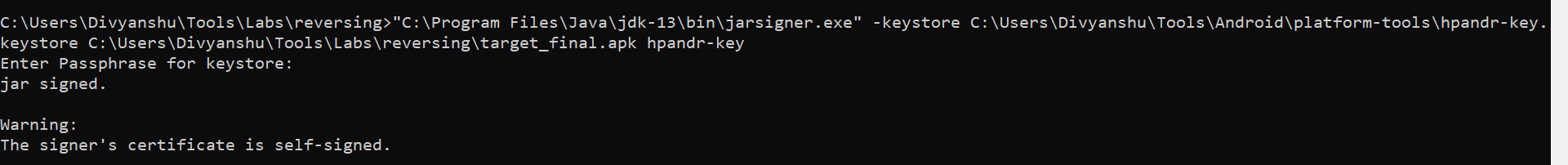
baksmali d classes.dexI recompiled the apk using apktool and signed it with my key (as shown in the below picture). You can find blogs, on how to generate your keys and used them for apk signing.
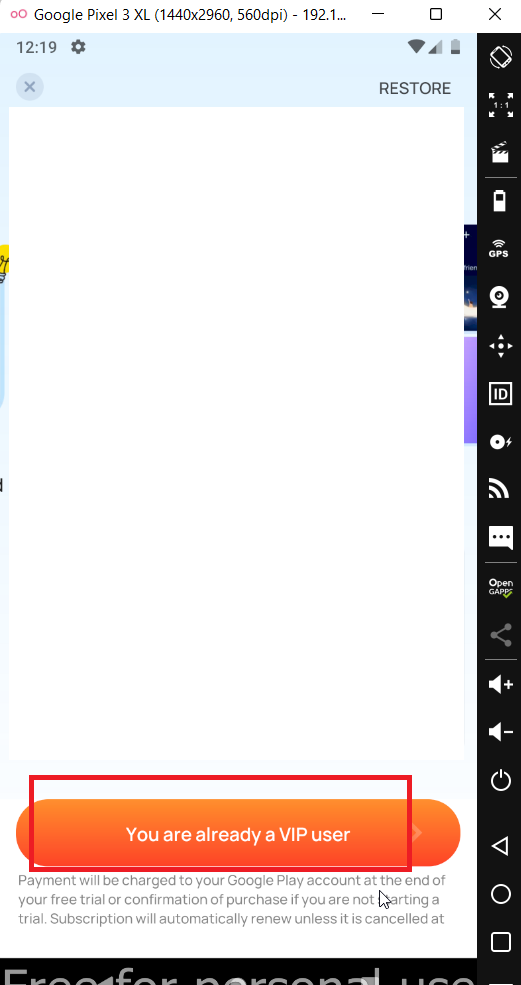
Then I just install it in the Genymotion Emulator to see if that works or not, and it worked like a charm!!
That’s It, for now, I will be writing the same type of android reversing series blogs in the future. Hope you guys like it.
